Trainer's guide
Co-authored by Timo Pagel
Instances
Make sure all participants have their own running Juice Shop instance to work with. While attempting challenges like RCE or XXE students might occasionally take down their server and would severely impact other participants if they shared an instance.
There are multiple Run Options which you can choose from. It is perfectly fine to run multiple docker containers on one host. They do not effect each other.
Customization
Especially in awareness trainings for management you might want to create a higher immersion by making the Juice Shop look like an application in the corporate design of the participants' own company. Juice Shop offers various customization options to achieve this.
Several custom configurations already come packaged with the Juice Shop source code, the two most sophisticated ones being 7 Minute Security and Mozilla.
In addition, you might want to disable all challenge notifications during awareness trainings to avoid distraction. The Quiet configuration demonstrates the necessary options to achieve this.
For a really sophisticated and immersive demo consider performing some Additional Browser tweaks. These will let you use OAuth2 login via Google and cast the illusion that coupon codes were actually tweeted by your customer's company.
Classroom hints
In a class room setup you have to find a way to distribute the URL of each instance to the participants. For small groups, it is probably fine to just spin up a number of containers and tell all participants which URL they have to use. An example to spin up 10 Docker containers on a UNIX based system is to run
for i in {10..19}; do docker run -d -p 40$i:3000 bkimminich/juice-shop; done
If you want to track progress centrally during the training, you might want to host a central CTF server where participants can post the challenges they already solved. You might consider turning off public visibility of the leader board on the CTF server unless you want to encourage the students to hack very competitively.
Hosting individual instances for multiple users
A solution to host and manage individual Juice Shop instances for multiple users is MultiJuicer. MultiJuicer is a Kubernetes based system to start up the required Juice Shop instances on demand. It will also clean up unused instances after a configured period of inactivity.
MultiJuicer comes with a custom-built load balancer. It allows every participant (or a CTF team) to use the same URL, but their traffic will always be sent to their own personal instance.
Registration at MultiJuicer is very straightforward for the users/teams. Messing with other instances is prevented by assigning a passcode to each of them which should only be shared among team members - or not at all for individuals.
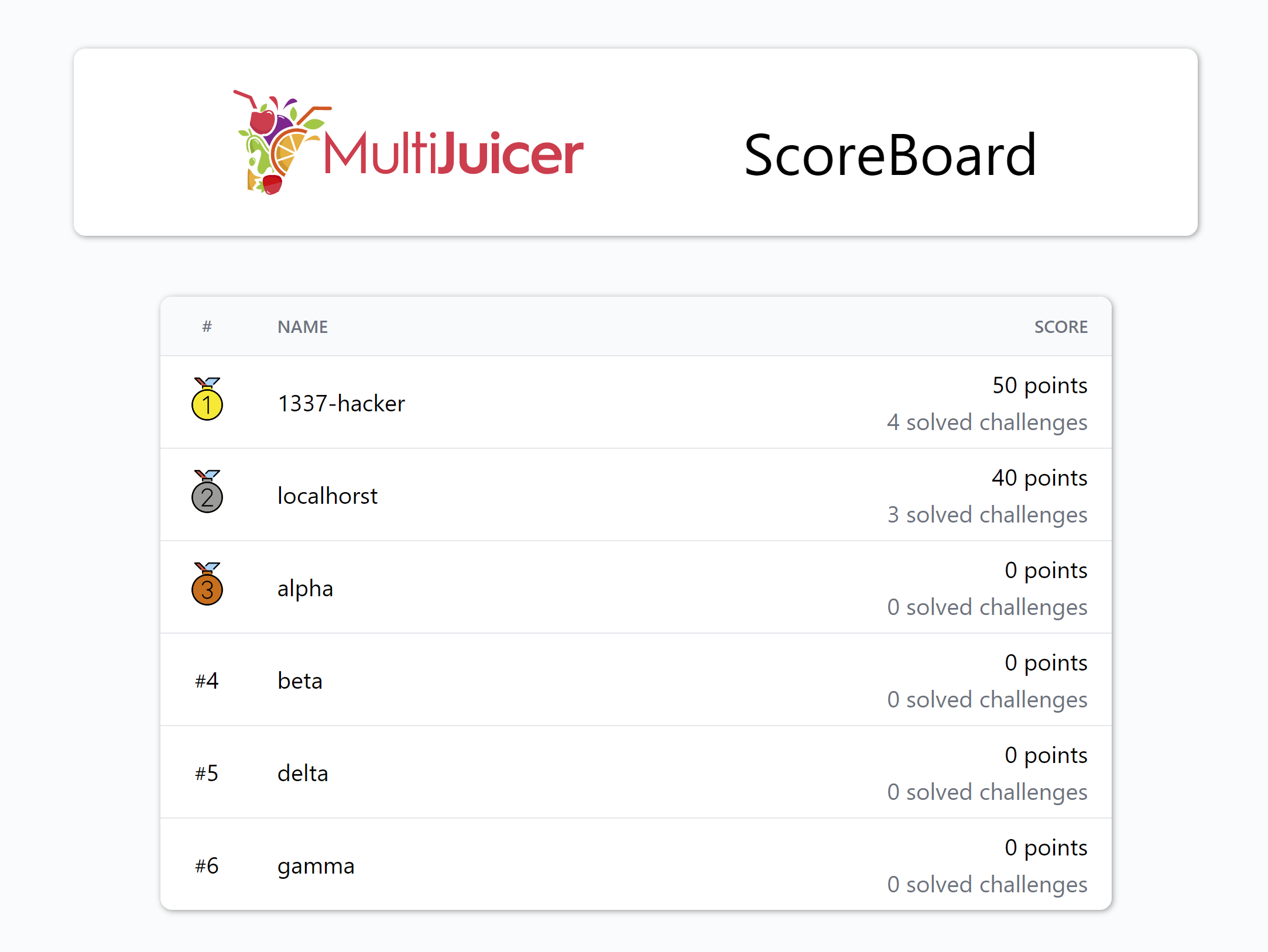
MultiJuicer comes with a rudimentary Score Board of its own, which allows teams to compare their progress through the Juice Shop challenges.
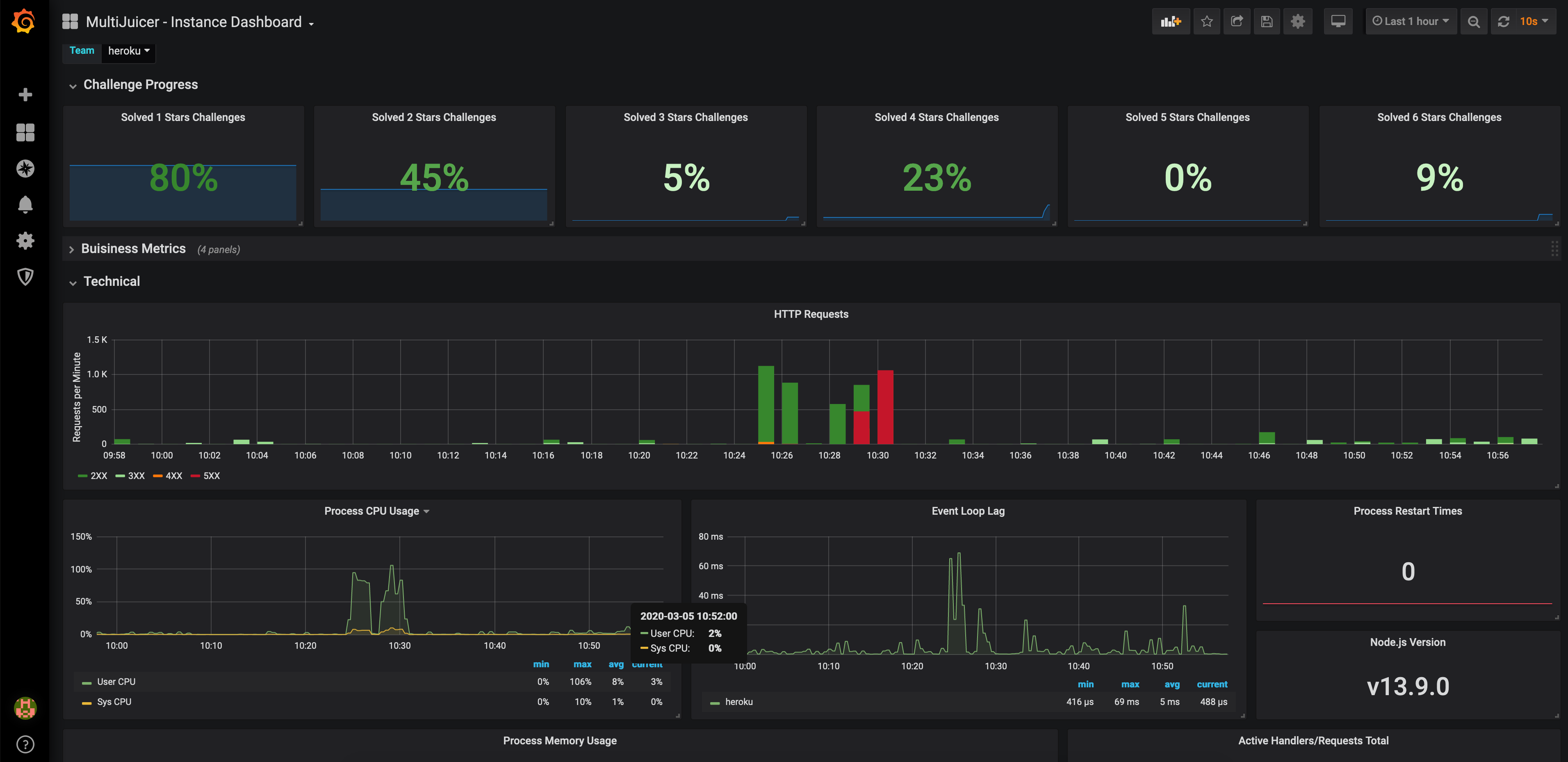
Another helpful feature for the trainer MultiJuicer is the optional dashboard which automatically consumes and displays metrics from each of its Juice Shop instances. It shows individual challenge progress along with other functional and technical stats and can be very helpful in troubleshooting as well.
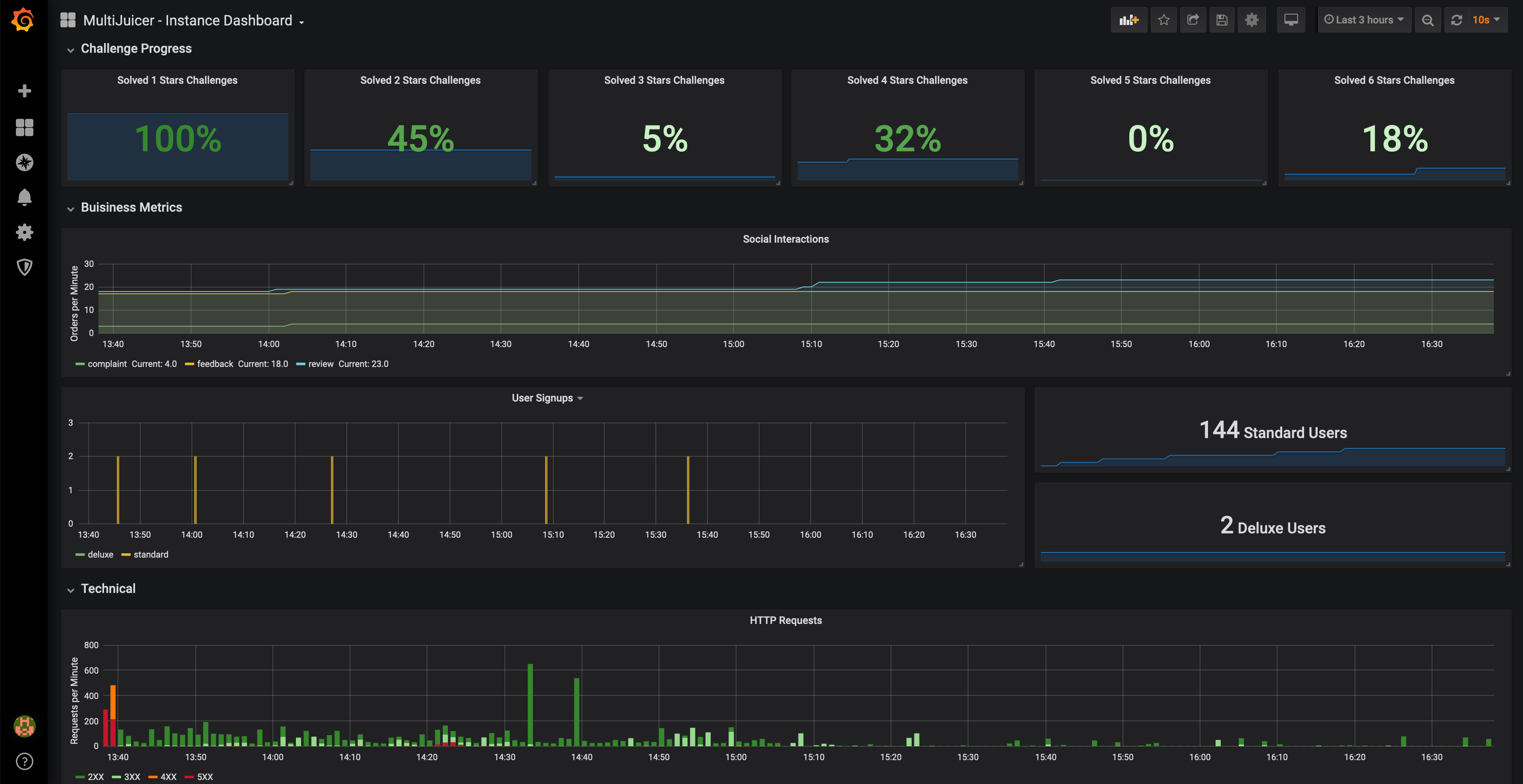
The MultiJuicer repository offers guidance on how to set up the system on different cloud provider platforms, such as Digital Ocean, OpenShift, AWS or Azure.
Existing trainings
One existing training which uses the Juice Shop for example is Timo Pagel's University Module. The structure mostly is as follows:
- Introduce a topic (e.g. SQL Injection)
- Let the participants try it out in the Juice Shop
- Show mitigation/counter measures
The 2nd semester web attack chapters of Björn Kimminich's IT Security Lecture follow a similar pattern of
- Introduction
- Timeboxed exercise
- Demonstration of the hack (for all who did not finish the exercise in time)
- Explaining mitigation and prevention
You can find more links to existing material in the Lectures and Trainings section of the project references on on GitHub.
Challenges for demos
The following challenges are well suited for live demonstrations in trainings or talks. You should always begin by showing how to find the Score Board ( ⭐ ) so you can then pick any of the challenge below to further demonstrate certain categories of vulnerabilities.
| Challenge | Category | Difficulty | Time for demo | Dependencies |
|---|---|---|---|---|
| DOM XSS | XSS | ⭐ | ⏳ | None |
| Confidential Document | Sensitive Data Exposure | ⭐ | ⏳ | None |
| Login Admin | Injection | ⭐⭐ | ⏳ | None |
| Privacy Policy | Miscellaneous | ⭐ | ⏳ | Log in as any user |
| Reflected XSS | XSS | ⭐⭐ | ⏳⏳ | Log in as any user and complete checkout process (to find the vulnerable tracking link) |
| Privacy Policy Inspection | Security through Obscurity | ⭐⭐⭐ | ⏳⏳ | Privacy Policy |
| Admin Section | Broken Access Control | ⭐⭐ | ⏳⏳ | Login Admin or Admin Registration |
| View Basket | Broken Access Control | ⭐⭐ | ⏳⏳ | Log in with two different users |
| Easter Egg | Broken Access Control | ⭐⭐⭐⭐ | ⏳⏳⏳ | Explain Poison Null Byte |
| Nested Easter Egg | Cryptographic Issues | ⭐⭐⭐⭐ | ⏳⏳⏳ | Easter Egg |
| Forgotten Developer Backup | Sensitive Data Exposure | ⭐⭐⭐⭐ | ⏳⏳⏳ | Explain Poison Null Byte |
| Forged Coupon | Cryptographic Issues | ⭐⭐⭐⭐⭐⭐ | ⏳⏳⏳⏳ | Forgotten Developer Backup and z85-cli installed or Forgotten Sales Backup or tracing coupons from Twitter back to https://github.com/juice-shop/juicy-coupon-bot/actions?query=workflow%3A%22Monthly+Coupon+Distribution%22 |
XSS demo
A particularly impressive showcase of XSS site-defacement combined with a keylogger is provided explicitly for live demos and awareness trainings:
- Install Docker.
- Run
git clone https://github.com/wurstbrot/shake-logger. - Run
cd shake-loggerand thendocker-compose up. - Turn on your speakers and make sure your browser is allowed to play sound.
- Open this link to launch the XSS demo (🔊).
- Use the application normally, e.g. doing a search and logging in with some user.
- In a new tab go to http://localhost:8080/logger.php to see that all user input was transmitted to a third-party server.
- Show the Network tab of the browser window with Juice Shop to see the
requests that are sent to the
logger.phpscript. - Reload the Juice Shop with
F5and use the application a bit more. - You will see that no more logging takes place as XSS payload was removed during the reload.
There is also a video recording available on YouTube: https://youtu.be/Msi52Kicb-w. This is a good fallback in case the Docker-based setup does not work for you.
Teaching automation of security tools
Only a few challenges in OWASP Juice Shop are explicitly expecting to utilize the power of automation, mostly in the form of some brute force attack. Quite a few more challenges are still well-suited for teaching the use of automated tools . The following table gives you an idea on complexity and expected time consumption for each of these, so you can plan your training accordingly.
| Tool | Description | Effort to automate | Execution runtime | Challenges (Auto-solve?) |
|---|---|---|---|---|
| OWASP ZAP Traditional Spider or Forced Browse with small (or bigger) OWASP DirBuster list | Finds /ftp folder with many misplaced files and /promotion (and direct /video) path with jingle video |
🧠 | ⏳⏳ | Confidential Document(❌), Forgotten Developer Backup(❌), Forgotten Sales Backup(❌), Misplaced Signature File(❌), Login Support Team(❌), Video XSS(❌) |
| OWASP ZAP Forced Browse with big OWASP DirBuster list | Finds /encryptionkeys directory with jwt.pub and premium.key key files |
🧠 | ⏳⏳⏳ | Forged Signed JWT(❌), Premium Challenge(❌) |
RaceTheWeb config (or custom Bash, Python etc. script) sending 10 sequential POST requests to Feedback API endpoint within 10 seconds |
Must pin captchaId and captcha from one initially received and solved CAPTCHA |
🧠(🧠) | ⏳ | CAPTCHA Bypass(✔️) |
Burpsuite (Community Edition) Repeater with Top Names Over the Last 100 Years into Password Reset API endpoint for email jim@juice-sh.op |
Contains answer to Jim's security question as 44th of Top 100 male names of 1919-2018. List needs to be manually prepared from HTML page. | 🧠🧠 | ⏳⏳ | Reset Jim's Password(✔️) |
RaceTheWeb config (or custom Bash, Python etc. script) sending 3 simultaneous POST requests to Like Reviews API endpoint |
Requests must be processed within 150ms time window to exploit race condition flaw | 🧠(🧠🧠) | ⏳ | Multiple Likes(✔️) |